This post presents an argument for starting any cybersecurity education program with the offensive techniques, even when the purpose of the training is to build defensive cybersecurity professionals.
EDIT: So this work is now officially published with some additional resources. Check out this post for the official paper and a video of the presentation.
Motivation for this Work
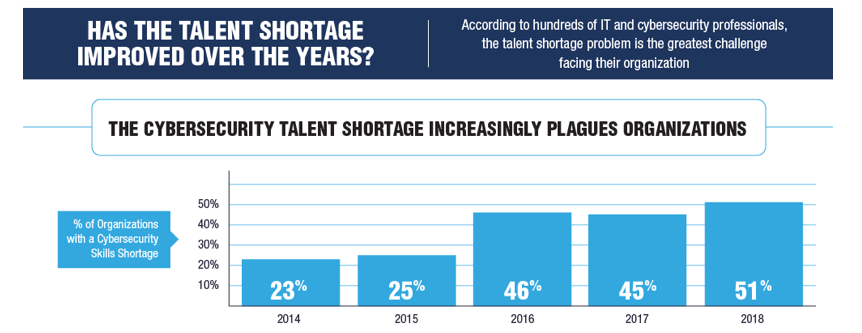
Over the past year, there have been numerous articles written on the subject of the gap of cybersecurity professionals like this, this, this, and this that include infographics like the one below. This shortage of cybersecurity talent has results in an increased in cybersecurity education in colleges, through bootcamps, and even programs for kids.
Due to this increased demand for cybersecurity training and my experience teaching cybersecurity classes and coaching cybersecurity clubs, I often receive questions on the best method of teaching cybersecurity. I feel very strongly that teaching offensive techniques are not only a vital part of any defensive cybersecurity training, but that these techniques should also be taught first, even when the primary purpose of the course is defensive training. I have laid out this argument several times over the past year, enough so that I felt it was worth putting into a public post. Ultimately, I am encouraged that the conversation [sometimes] has moved past arguing about the value of offensive training at all and now simply to which type of training simply should be taught first.
In order to support my opinions in this article, I spent quite a bit of time researching other people’s opinions on cybersecurity programs, but I really could not find a lot of scholarly[ish] works on offensive training. I have included what I could; however, if you have any good resources on this topic, please let me know.
Part 1: Why You Should Start by Teaching Offensive Cybersecurity (Hacking)
Why we should teach offensive cybersecurity first.
- The majority of the skills are the same.
- Offensive techniques are more fun so better for developing life-long learners.
- Offensive techniques establish a better cybersecurity mindset.
- Offense is not harder than defense (at an introductory level).
The majority of the skills are the same.
Are the below training topics for offense or defense?
- Command line tools and proficiency (grep, find, netstat, chmod, etc.).
- Network captures and parsing (tcpdump, wireshark, pcaps).
- OSI Model and network protocols (http, smb, ftp, ssh, dns, and so on).
- Vulnerability scanning (nmap, google hacking, whois, dig).
- Scripting (bash, python, PowerShell).
- Cryptography foundations (encryption, hashes).
- Binary Analysis (C, assembly, the stack, insecure functions, gdb, immunity).
- Forensic artifacts (logs, recovering deleted files, important system data).
Exactly - they’re both. Everything above is foundational knowledge and concepts for any cybersecurity training program whether offensively or defensively focused. The method of teaching or tool used to teach can change (the how), but the knowledge (the why) is the same. Once the student understands the concepts, they can easily adapt the knowledge to any specific tool (and even the tools are the same for most of these concepts).
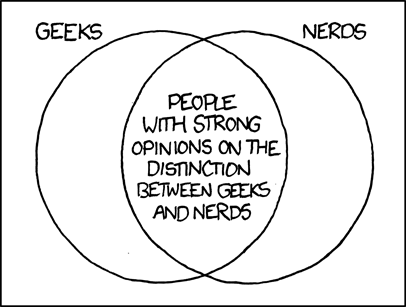
Little as been published specifically on offensive compared to defensive cybersecurity, and what has been published (like this, this, or this) focused on mentality or policy. If you know of any reference discusses offensive vs. defensive security tools and techniques, please let me know. I was hoping to find a great Venn diagram on the subject but could not. Instead, I will give you this xkcd comic (it is more relevant if run the command)
sed -e 's/nerd/red team/g;s/geek/blue team/g' <<< venn_diagram.
Offensive techniques are more fun and, therefore, better for developing life-long learners.
Offense sells tickets. Defense wins championships. - Bear Bryant
I think it is fairly universally accepted that offense is more fun and exciting than defense; this is no different in cybersecurity (and is evident by the quirky hacker included in so many popular shows). Even though defensive operations are the primary focus for most cybersecurity experts, we should leverage the popularity of offensive operations to build excitement about cybersecurity training and develop a foundation for independent life-long learning: what I like to coin as passion. I’ve previously written about the importance of building passion but am going to expand upon my previous discussion by first explaining why life-long learning is so important in cybersecurity, and I will then describe how offensive techniques, through the use of gamification, are the best for developing life-long cybersecurity learners.
The importance of Life-long Learning in Cybersecurity
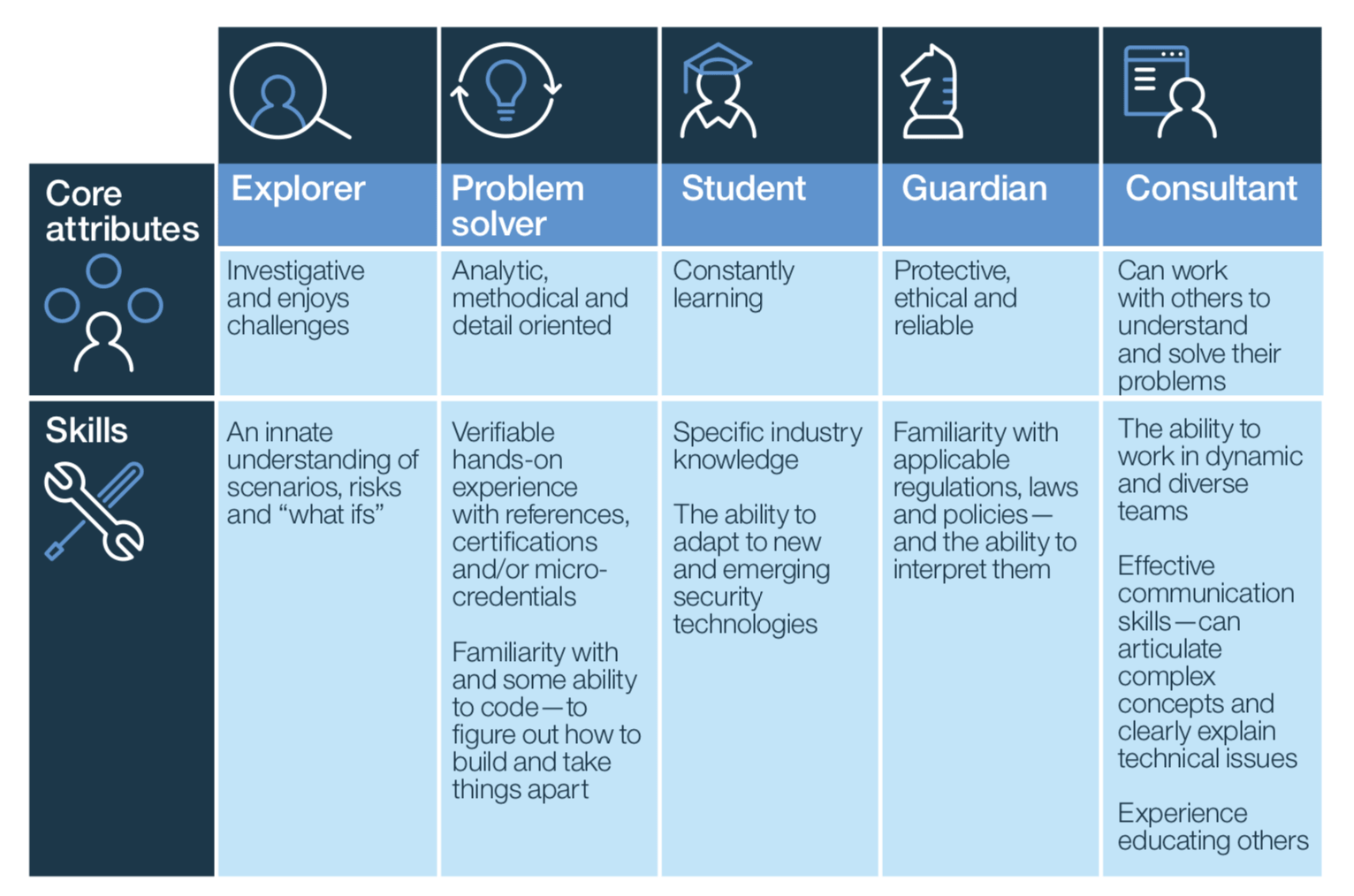
The cybersecurity industry is moving so fast that the tools, techniques, and best practices taught today will be obsolete in just a few years. Kevin Curran references this when he says “I cringe when some news outlets reuse parts of earlier interviews I have done and stated ‘facts’ but best practice may have moved on since the time I made the initial comment.” He later references the old (2016) best practice of mandatory password changes that is already recognized as obsolete. The point here is no cybersecurity program is solely enough; student must to continue learning for the rest of their career to be successful. Industry has quickly identified this requirement in cybersecurity professionals. Both this Economist paper and this IBM Institute for Business Value paper specifically address the need for life-long learners to fill and address the current cybersecurity gap. Look at the below figure from the IBM article. Investigative and enjoys Challenges and Constantly learning - these are exactly the attributes we are need to develop in future cybersecurity practitioners.
Using Gamification Helps Develop Life-long Learners
How do you develop life-long learning (this internal passion)? Several articles try to tackle this issue.The Oxford Handbook of Lifelong Learning identifies several characteristics like “technical curiosity and interest”, “learning that includes feedback”, “encountering novel problems”, and “a positive feeling about learning” all as attributes that contribute to developing life-long learners. In terms of resources, the article says, “People do the learning, and must be motivated and take action to learn." “Preparing Students for Lifelong Learning,” by J. Dunlap addresses developing an intrinsic motivation (passion) as a primary contributor to continued and life-learning: \
“Intrinsic motivation strategies are based on the idea that students will expend more effort on tasks and activities they find inherently enjoyable and interesting, even when there are no extrinsic incentives.”
Having fun through enjoyable and interesting cybersecurity resources builds this intrinsic motivation that will continue to move our cybersecurity students to learn even after the course has ended. How do we create exciting and enjoyable cybersecurity challenges? Through the use of gamification.
Offensive Cybersecurity is Better for Gamification
Several scholarly articles have been written on the value of gamification, specifically in Cybersecurity education. Juho Hamari is the most cited author recently on gamification. “Does Gamification Work?” by J. Hamari Et al. is a literature review of 24 peer-reviewed empirical studies on gamification. This paper concludes that, “according to a majority of the reviewed studies, gamification does produce positive effects and benefits." Another paper, “Challenging games help students Learn,” by J. Hamari Et al. demonstrates that game engagement has a clear positive effect on learning and that is best achieved in challenging games. There are numerous other academic papers, such as “Cybersecurity: Teaching through Gamification by Gonzalez Et al.", and even commercial papers, like this Circadence whitepaper, that support gamification being an important learning tool, particularly for cybersecurity education.
So gamification helps students learn cybersecurity but what exactly are we gamifying? I could really go off on a tangent here on the various cybersecurity gamification resources and methods (this post contains a little more information), but I will instead focus on some recent gamification research. “Cybersecurity: Teaching through Gamification” by Gonzalez Et al." provides a taxonomy for classifying cybersecurity gamification resources as well as classifies some the most popular resources (listed in the below table).
Twice as many of these resources are classified as attack-only with regards to content orientation than defense-only. More significantly, there are just as many combined (Hybrid or Attack/Defend) content oriented resources as attack or defense only - supporting my earlier point that these are really the same skills. “Cybersecurity Education through Gamification – the CTF Approach,” by C. Li Et al. also looked at gamified cybersecurity resources. All but one of the resources (Cyber Patriot) included offensive components with the majority being hybrid resources. Why? Because the offensive (hacking) is cool, fun, and teaches the same skills. These techniques are more exciting which makes them more engaging and, therefor, the best type for developing life-long learners.
Offensive techniques develop a better security mindset.
The defender needs to find and fix all vulnerabilities whereas the attacker needs only to find and exploit one to get in. - Me (a paraphrased common sentiment)
The concept of “the security mindset” has been around for almost a decade. This idea started circulating in the late 2000s with T. Kohno’s “How to think like a security professional”, Bruce Schneier’s Wired interview, “Inside the Twisted Mind of the Security Professional”, and Ed Felten’s response, “The Security Mindset and ‘Harmless Failures’". This concept is further explained in the video below, but, to borrow a quote from Bruce,\
“This kind of thinking [the security mindset] is not natural for most people. It’s not natural for engineers. Good engineering involves thinking about how things can be made to work; the security mindset involves thinking about how things can be made to fail. It involves thinking like an attacker, an adversary or a criminal. You don’t have to exploit the vulnerabilities you find, but if you don’t see the world that way, you’ll never notice most security problems.”
Based on my previous experience teaching both offensive and defensive cybersecurity, I feel the security mindset is really the offensive security mindset. Students that grow up defense-only do not think this way. They focus on checklists that they use to defend assets. John Lambert has written on this topic extensively so I will not rehash his argument but rather use his favorite saying,\
“Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win.”
But it’s more than just this assets vs. graph mentality - it’s also this idea that a single compromise means failure. I have seen this often, particularly in young defenders. They would spend months preparing for some large event, such as CCDC or the capstone in CS482. They would follow their assessment procedures, implement their security primitives, and clean their various boxes with the taught defensive techniques. The competition would start and, eventually, an attacker would gain access through some overlooked vulnerability, missed rootkit, or [the worst] a silly phishing email. The students' reactions generally varied from the dejected dog to being ready to flip the table. I am using hyperbole here but being compromised really impacted my students' psyche.
The reality is compromise is inevitable. My students' would rebound and start mitigation procedures but generally focused on symptoms - block the outbound IP, kill the bad process, look for signatures of additional compromise. This remediation would then turn into some increasingly escalating game of whack-a-mole.
What does this look like from the red team perspective? Well, they also spent months building their images, embedding rootkits, and testing exploits. Competition starts, and they launch the first exploit. Blocked. They then try a rootkit - it was found and removed. Vulnerability? Patched. They slowly work their way through their entire list of pre-configured exploits and nothing works. Do they give up? Heck no! Why did the second rootkit not work? Was it really found or are the defenders just blocking the outbound communication method? The red-teamer then tries switching to another method like DNS. Still no callback. Ok. Maybe they can not get out directly but can instead pivot through another box. Forty failures, and they keep trying. They use this cycle of testing, troubleshooting, and problem solving until eventually they get in.
Of course these are generalizations and my own assessments, but I believe starting with offensive techniques help establish not only Schneier’s security mindset but also a mindset of resiliency through troubleshooting and problem solving. Look at the mantra for Offensive Security’s Introductory Ethical Hacking Course, PWK - it’s “Try Harder”. Go to live support because your stuck with a box. Their response? Try Harder. Post a question on the forum? You’ll either get a “Try Harder” or “enumerate more”. Offsec wants its student to internalize this motto so much they put it on stickers, made it a song, and even put it inside their certificate folder.
The American Psychological Association identifies “avoid[ing] seeing crises as insurmountable problems” and “keep[ing] things in perspective” as keys to building resilience. When You Mess Up, Get Up looks at what causes resiliency and identifies two key components: motivation to continue to try and coping mechanisms for failure. For motivation, the article states most people display an innate enjoyment for activities that provide at least a moderate challenge (same as discussed above), but it also says,\
“But when we try, fail, try something else, fail, try again and ultimately succeed, we get a nice kick from our dopaminergic reward system. This is how goal accomplishment leads to improved motivation and allows for positive self-reflection when facing future difficulties (I got through a tough patch before, I can do it again).”
The “Mess Up, Get Up” article also identifies three coping methods (explained in significantly more detail in “Stress Management” by S. McLeod). The most successful method, as backed by several peer-reviewed studies, is problem-focused coping that tackles the problem in a practical way through problem-solving.
Offensive techniques build a more resilient mindset since the inherent expectation is to often and repeatedly fail. This cycle of repeatedly failing helps develops better problem-focused coping methods, and the eventual success provides both a chemically induced increase in motivation as well as positive self-reflection which helps tackle future, more difficult challenges. Conversely, the defender rarely fails during training, and, therefore, does not have positive self-reflection or develop successful coping methods to handle future failures.
Mind Blown.
Offensive is not harder than defense [at an introductory level].
Just to recap since this has been a rather long post, I hope to have convinced you by this point that:
- Offensive and defensive cybersecurity use many of the same skills
- The cybersecurity requires life-long learners
- Gamification helps develop life-long learners
- Offensive techniques are best to gamify because they are most exciting and engaging
- Offensive techniques are also best to start with because they build the best growth mindset
Even once I have someone convinced of all the bullets above, I still get push back because this methodology goes against the traditional establish paradigm for teaching cybersecurity. The most common argument I get next is that offensive is harder than defense. As such, you can not start with the harder subject because it will discourage or frustrate your students, and they will quit or fail. I hopefully already disprove this argument somewhat with the discussion of offensive and defensive requiring many of the same skills, but I will dive deeper into why this common misconception exists as well as why it is not true.
Offensive cybersecurity training is not as difficult as real world penetration testing
As I argued above, the skills required by offensive and defensive cybersecurity experts are mostly the same. Looking at jobs on CyberSeek, there are ~10k offensive jobs out of over ~70k entry and mid-level jobs (a little less than 15%). CyberSeek lists Penetration & Vulnerability Tester as a mid-level job, and all offensive jobs are only mid-level+ positions.
The perception of the offense being more difficult exists because penetration tester, the introductory offensive job, is not an entry-level position like other, defensive cybersecurity positions. As such, a starting offensive cybersecurity profession has to be mid-level and, therefore, is certainly more competent than an entry-level defensive cybersecurity professional. Also, because of the limited availability of these positions, they are only filled by highly talented (above average) cybersecurity professionals. Again, this causes a perception of expertise not necessary required by entry level penetration testers.
Finally, we do not have to use the same level of techniques required by professionals in training. For example, real pentesters need to be capable of developing custom, real world exploits. However, we do not need custom, real-world exploits for training (at least, realistically difficult exploits). Instead, we can tailor the level of the challenges in offensive training exercises, therefore making it the best for teaching introductory cybersecurity education.
This issue has been been addressed by a lot of recent research. Look at picoCTF for example or the actually research paper on PicoCTF. Other examples are Carlsie’s et al.’s Using CTFs for undergraduate Cyber education, Schreuder’s and Butterfield’s Gamification for Teaching and Learning Computer Security in Higher Education, and even this past year’s ShmooCon talk on methods for teaching pre-college students at Penn State University.
The end result of all this research is that offensive gamification (CTFs) is a great and proven method of engaging and teaching basic cybersecurity concepts as long as the challenges are appropriately balanced with hints to prevent frustration. Ultimately, the above discussions makes offensive techniques the best for teaching cybersecurity education, even when the goal is to build defensive security experts, because both techniques develop the same skills and offensive techniques are the best to build lifelong cybersecurity professionals, the end goal of any cybersecurity program.