Teaching offensive cybersecurity techniques builds better defenders. While I’ve discussed this before (like in this post), this vulnerability disclosure is a great vignette for highlighting why teaching offensive cybersecurity techniques are so important for building defensive cybersecurity professionals as well as why bug bounty programs are so critical for improving the defensive posture of your systems.
Offensive cybersecurity training has changed my mindset towards how I interact with systems, and I am a significantly better defender because of this offensive training. I am certainly convinced this is true, but I hope this story helps convince you more of the value of offensive training. A little over two years ago, I took my first offensively oriented course, and I have since accidently found, reported, and helped fixed at least five significant vulnerability on several different systems - way more than the zero I had found in the previous decade of solely defensively based cybersecurity training. While I am sure other factors have contributed to these vulnerability discoveries, I feel this recent disclosure is a great example of the importance of offensive cybersecurity mindset (as opposed to the specific skills) as well as a good example of the value of bug bounty programs.
First and foremost, this discovery was nothing special. I was in a knowledge management system and viewing an important document about my future assignment (job) that was being displayed in a smaller imbedded window. I wanted to save a copy of the document (this window did not have implicit save functionality), so I right-clicked copy link address and pasted the URL (https://███/portal/viewrfo.aspx?offasgid=MjAwODAyMTg1Ng==) into a new tab. As soon as I pasted it, my cybersecurity spider-senses went off. I’m sure everyone who has ever participated in a CTF or offensive cybersecurity training can already see where this story is going. A GET parameter that contains id and a value that end in =. Knowing that strings that end in = are generally base64 and should be decoded is essentially instinct at this point ingrained into me from just about every CTF or offensive training course I have ever taken. So I decode it, see what is clearly date-based numeric IDs, and the rest is a fairly simple CTF problem at this point.
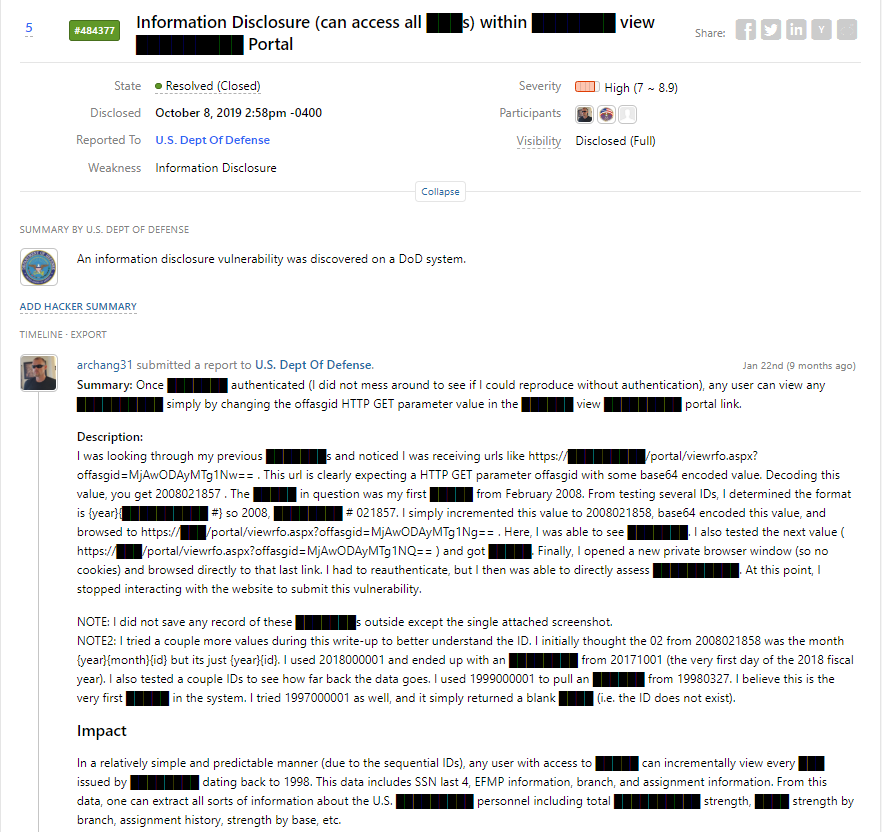
You can read the full vulnerability disclosure here, but the skills needed to find this vulnerability were not particularly complicated. One simply needed to understand how to parse HTTP GET requests and Base64 encoding/decoding. My students in their second week of training at the Fullstack Cyber Bootcamp can already have the skills to find this vulnerability. But the impact?
Any user with access to █████ can incrementally view every ███ issued by ████████ dating back to 1998. This data includes SSN last 4, EFMP information, branch, and assignment information. From this data, one can extract all sorts of information about the U.S. █████████ personnel including total ██████████ strength, ████ strength by branch, assignment history, strength by base, etc.
I know there are quite a few things blacked out, but I am sure you can infer what was accessible. Pretty significant stuff. This example is also not just a one-time fluke. This is actually my third HTTP GET parameter vulnerability I have discovered in the past year on three different systems - all of which were found accidentally while interacting with a system that I was simply using as a regular user (i.e. I was not doing a pentest or even thinking initially about looking for vulnerabilities). I have known the skills required to find these vulnerabilities since my CS undergraduate courses back in the mid-2000s, so why am I just noticing these all vulnerabilities now?
It all comes back to the security mindset (I wrote even more extensively about this mindset in this paper, Ch. 4.1). I am sure I have interacted with links with even worse URL parameters before and never even noticed, but I was always approaching these system with the mindset of “How can I use this system (make this system work)" verses “How can I make this system fail”. This is the crux of Bruce Schneierd’s security mindset and why teaching offensive cybersecurity training as early as possible is so important. Instill this offensive mindset in our cybersecurity defenders, teach them how to ethically approach these vulnerabilities when they start finding them, and then focus on the more traditional defensive cybersecurity skills. This is how we best build the cybersecurity defenders we are so desperately short of right now.
Bug Bounty Benefits (Vulnerability Disclosure Programs)
They protect users so they do not fear reporting and enable users to easily report, and this easy process incentives users to search for and report additional vulnerabilities.
So I found what is clearly an issue, what do I do next? Initially, I was a little worried I could get in trouble from my vulnerability testing because I accessed records I did not have explicit permission to (I actually was covered by the VDP but did not know it at the time). More significantly, I was worried the vulnerability disclosure process would be a pain. In my previous experience with finding a vuln. on a government system, getting in touch with the right person was quite a challenge. I emailed some POC who put me in contact with the web content creator who then had to figure out who was responsible for maintaining the infrastructure, etc. etc. It took quite a bit of back and forth while repeatedly explaining myself to get to someone who just responded with “thanks - we’ll look into it” and that was it.
So this time, I start asking around and quickly found out about the new (at the time) DoD Hackerone Vulnerability Disclosure Program. Awesome. I filled out a form, added some screenshots, and had a response almost immediately (within 12 hours). In fact, since it was so easy (and I was clearly covered by the VDP agreement), I decided to take a deeper look at the site. I found 3 more accepted vulnerabilities (2 classified as high) in 3 hours of poking around; less time then I spent just trying to get in contact with the right person on my previous vulnerability disclosure. One vulnerability fix was turned into four simply because of how easy it was to use the program. I was happy because my time was spent giving back to the system (after-all, I was helping to protect my own data) instead of figuring out how to report these issues, and the system owner was happy because more vulnerabilities were discovered and fixed. Bug bounties are a win-win for both parties involved.